What do we mean by SNMP Scanning? For the purposes of this article, it means scanning a range of IP addresses to see what devices are running SNMP servers. Some people call this SNMP Community Name guessing or bruteforcing.
What is SNMP and what is it used for? SNMP stands for Simple Network Management Protocol. It's used by network devices like routers and switches to report information about the device. Even a Windows computer can be made to divulge information using SNMP! (Windows does not install it by default). This information can be device information like temperature, packet counts or packet statistics or even IP addresses of devices connected to the device. The info is arranged in a heirarchical order somewhat like directories on a hard drive.
SNMP comes in 3 flavors or versions: 1, 2c and 3. Most devices support 1 and 2c, while newer devices will support v3 and usually have backwards compatibility with versions 1 and 2c. Versions 1 and 2c are very similar and report data to a client if the client includes a simple plain text password-like phrase called a 'community name'. We're going to limit our discussion to v1 and v2c.
SNMP usually runs on UDP port 161. Some people like to put it on an alternate UDP port to avoid what we are going to do in this article. Since it's a UDP based protocol, there is no full connection, so when we talk to an SNMP server it won't respond to us unless the question we are asking is correct. There are two essential parts of the question: the MIB item we are asking for and the community name (password) to get it. Both have to be correct to get a good response.
Back to the point of this article. How do you find the devices in your network running SNMP? One way is to do a Port Scan of every device in the IP range on port 161. This might work, but since SNMP is UDP you are depending on the targets returning an ICMP Port Unreachable message to you if the device is NOT running SNMP. This is a lot to ask, especially if the devices have a firewall or are set to not reply with ICMP. You run the risk of lots of false positives with port scanning.
Another way is to use a specialized tool called SNMP Dictionary Attack which is part of NetScanTools Pro. This tool can make an SNMP query to each IP address and it can send known or common community names to the devices. If you are a network administrator, you already know what the community names of your devices are, so here's a shortcut that you may want to try (if not, then skip this). Locate dctnry.txt in your NetScanTools Pro installation directory and open it with notepad. Enter your common community names at the beginning of the list, one per line and save it (we are going to improve this soon).
Using NetScanTools Pro to scan for SNMP servers on devices. Start NetScanTools Pro and locate the SNMP tools under the Tools left panel group. Select Dictionary Attack under the dropdown list labeled Select SNMP Action. Press Perform Action (no other settings are necessary). This opens the tool.
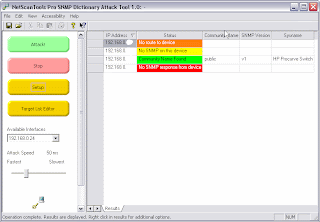
Now press the Target List Editor button on the left panel to open the editor. You can do one of several things here. You can enter IP addresses one at a time or you can define a range of IPs or you can import a list of IPs. The bigger the list, the longer the scan takes - recommend 256 or less IPs. Once you have created your list press OK and then press Setup. In Setup you can define the SNMP version(s) you want to use. If you choose both v1/v2c, it takes twice as long to scan. You can also adjust the time to wait for an SNMP response. Once you are satisfied with the values, press OK and now we are ready. Put the 'Attack Speed' in the middle range and press the 'Attack' button.
The scan proceeds with the results being presented in the grid as they are found. If the device responds to the SNMP queries, you will see 'Community Name Found' along with the community name, version and system name. If not, you will see 'No SNMP on this device' if an ICMP message came back. You may also see a definitive 'No route to device' if you are on the same subnet as the device. If you edited the dictionary list first, this process will go pretty quickly if you are on the same subnet, but it may take awhile if you are scanning devices outside your subnet.
You can watch the scan status on the lower bar. This tool will work best on the same subnet as the devices, but it is not limited to that subnet (the demo version is limited to the local subnet). While you watch it scan, if the device status is blank, it will continue to try community names until it exhausts the list or the device responds.
When you are done or when you feel the scan has gone on long enough, you can review the results. You should be able to see which devices are running SNMP and their community names.
This is a brute force password guessing tool that will show SNMP responses if the device is running SNMP and you have the correct community name. It scans a list of IP addresses and tests them with multiple SNMP queries in an attempt to get a response. It can take awhile and the community name may not be in the dictionary, so you may not be able to find the community name. We have created a fairly comprehensive list and it does cover many common passwords like the default 'public' and 'private'. Try out the tool in our demo or if you have the full version, give it a try. The demo is here: http://www.netscantools.com/nstprodemorequest.html
As with all scanning tools, we must warn you that your actions may be construed as hostile and may violate local laws. So you need to limit your scans to your own systems or have the permission of the IP address range owner before scanning. There will be lots of traffic directed toward the SNMP port, so intrusion detection systems (IDS) will see it. This is not a stealthy scan operation.
No comments:
Post a Comment