It seems to me that not too many people are working during the last two weeks of the year - especially this last week. The east coast was hit with a huge snowstorm, so maybe that has something to do with it.
Happy New Year!
A look at all things to do with NetScanTools® Products. Inside you will find tips and comments about using our programs and even off topic comments.
Tuesday, December 28, 2010
Tuesday, December 21, 2010
IPv6 eliminating NAT
I just saw an IPv6 tweet where the guy said he set up IPv6 DNS entries for all his home machines. He can now connect to them directly from his office to any home machine. He was happy to eliminate NAT.
I realize that you don't need NAT when your computers can all have their own IPv6 address - but NAT does provide some safety - think about it:
Now anyone knowing those IPv6s can contact (hack) his machines that are now sitting directly on the internet. Kind of like going back to the mid 1990s. IPv4 NAT was keeping him safe from alot of hazardous traffic that will now hit each PC directly...
Kirk
I realize that you don't need NAT when your computers can all have their own IPv6 address - but NAT does provide some safety - think about it:
Now anyone knowing those IPv6s can contact (hack) his machines that are now sitting directly on the internet. Kind of like going back to the mid 1990s. IPv4 NAT was keeping him safe from alot of hazardous traffic that will now hit each PC directly...
Kirk
Monday, December 20, 2010
December News
I've been pretty busy this month and I haven't updated the blog much - I hope to provide more timely updates in 2011. V11 status: All the tools from NetScanTools Pro v10 have been transferred to v11 and I'm working on finishing tooltips and icons along with general cleanup of things as I run across them.
The latest December newsletter was published last week. You can find it on our website at http://www.netscantools.com/newsletters.html - there is one very important thing in there that I will address here. In version 10.98.1 I changed the manifest so that USER level accounts could run the program without logging in as administrator on Windows 7-64 bit (this does not seem to be an issue on Win 7-32). When you run a 32 application like NetScanTools Pro on Windows 7-64, it uses a portion of the registry called HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Northwest Performance Software, Inc. which contains a redirected part "Wow6432Node". Users do not have privileges to change this key subtree and even if you login under an administrator account, the keys in this tree cannot be changed. So in order to apply registration information or change the maintenance plan expiration date, you have to right click on the NetScanTools Pro icon and select 'Run as administrator' to all the program to have full access to the keys.
The latest December newsletter was published last week. You can find it on our website at http://www.netscantools.com/newsletters.html - there is one very important thing in there that I will address here. In version 10.98.1 I changed the manifest so that USER level accounts could run the program without logging in as administrator on Windows 7-64 bit (this does not seem to be an issue on Win 7-32). When you run a 32 application like NetScanTools Pro on Windows 7-64, it uses a portion of the registry called HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Northwest Performance Software, Inc. which contains a redirected part "Wow6432Node". Users do not have privileges to change this key subtree and even if you login under an administrator account, the keys in this tree cannot be changed. So in order to apply registration information or change the maintenance plan expiration date, you have to right click on the NetScanTools Pro icon and select 'Run as administrator' to all the program to have full access to the keys.
Wednesday, November 24, 2010
Black Friday/Cyber Monday Sale
Check out this page for savings of up to 50% on our software.
http://www.netscantools.com/blackfridaysale.html
http://www.netscantools.com/blackfridaysale.html
Friday, November 19, 2010
NetScanTools Pro 10.98.1 is Now Available
Yesterday we released the latest installed version of NetScanTools Pro 10.98.1 and today we released the USB version patch. Both are now ready for you to update to the latest version. That is if you have an active maintenance plan.
Changes in this new version relate to starting NetScanTools Pro on Windows 7 or Vista where the account is running under USER privileges instead of Administrative privileges. When you tried to start previous versions of NetScanTools Pro under USER privileges, you would see a message asking you to supply the administrator account password so you could proceed and run the program. Clearly not optimum, so we identified the issue and corrected it. NetScanTools Pro will now start on USER privileges accounts.
There are two small issues that you may run into: on both the installed and USB versions the TimeSync function will not allow you to change your computer clock. That's because user privs are not enough to do it. The other issue is a little more of a problem on the USB version. Because the portable version of WinPcap requires adminstrative privileges to operate, any NetScanTools Pro tools that depend on WinPcap cannot be used. This does leave you with quite a few tools, but it is clearly not a preferred situation.
How to get the latest version: Click on Help/Check for New Version and login. You must have an active maintenance plan. If your maintenance plan has expired, please see this web page for information on reactivating it:
http://www.netscantools.com/nstpromaintenance.html
Changes in this new version relate to starting NetScanTools Pro on Windows 7 or Vista where the account is running under USER privileges instead of Administrative privileges. When you tried to start previous versions of NetScanTools Pro under USER privileges, you would see a message asking you to supply the administrator account password so you could proceed and run the program. Clearly not optimum, so we identified the issue and corrected it. NetScanTools Pro will now start on USER privileges accounts.
There are two small issues that you may run into: on both the installed and USB versions the TimeSync function will not allow you to change your computer clock. That's because user privs are not enough to do it. The other issue is a little more of a problem on the USB version. Because the portable version of WinPcap requires adminstrative privileges to operate, any NetScanTools Pro tools that depend on WinPcap cannot be used. This does leave you with quite a few tools, but it is clearly not a preferred situation.
How to get the latest version: Click on Help/Check for New Version and login. You must have an active maintenance plan. If your maintenance plan has expired, please see this web page for information on reactivating it:
http://www.netscantools.com/nstpromaintenance.html
Wednesday, November 17, 2010
Managed Switch Port Mapping Tool - What is it?
Do you have a network switch? Did you know that you may be able talk with it in ways OTHER than through a web browser?
Before web interfaces on network switches became popular, there was CLI (command line interface) and SNMP for managing the switch. Both of those methods can return a wealth of information about the switch and it's current state. If you have ever looked at a heavily populated network switch you would see that in all probability there are lots of wires going into those jacks on the front. And even more disturbing is that those wires are often the same gray color. How do you tell them apart and how do you know where they go?
That's where the Managed Switch Port Mapping Tool comes in. If you have SNMP enabled on that switch and you know the access credentials and your IP address is allowed to manage the switch (alot of 'ifs', I know), then our tool will most likely be able to 'map' or show the assignment of devices to the physical jacks on the switch.
The Managed Switch Port Mapping Tool is separate from NetScanTools Pro. They both can be purchased separately and both can be used without the other present.
Those are the basics. I'll be talking more about specifics in the near future. If you want to learn more now, please visit http://www.switchportmapper.com and http://www.netscantools.com/spmapmain.html
Try it out for yourself. There is a 30 day free trial available from either of those sites.
Kirk
Before web interfaces on network switches became popular, there was CLI (command line interface) and SNMP for managing the switch. Both of those methods can return a wealth of information about the switch and it's current state. If you have ever looked at a heavily populated network switch you would see that in all probability there are lots of wires going into those jacks on the front. And even more disturbing is that those wires are often the same gray color. How do you tell them apart and how do you know where they go?
That's where the Managed Switch Port Mapping Tool comes in. If you have SNMP enabled on that switch and you know the access credentials and your IP address is allowed to manage the switch (alot of 'ifs', I know), then our tool will most likely be able to 'map' or show the assignment of devices to the physical jacks on the switch.
The Managed Switch Port Mapping Tool is separate from NetScanTools Pro. They both can be purchased separately and both can be used without the other present.
Those are the basics. I'll be talking more about specifics in the near future. If you want to learn more now, please visit http://www.switchportmapper.com and http://www.netscantools.com/spmapmain.html
Try it out for yourself. There is a 30 day free trial available from either of those sites.
Kirk
NetScanTools Pro and User Privileges
Yesterday an astute user pointed out that if you start NetScanTools Pro 10.98 on Windows 7 in a USER privileges account, the operating system asks that you login with an administrator account password to allow the program to run.
NOT GOOD! You should at least be able to run the program from that type of account without jumping through hoops. So I quickly traced the issue to the MANIFEST. You programmers out there know about this. In it were commands asking for higher privileges than we really need, so I think we are going to have a new minor, minor revision on Thursday. Beside fixing that little problem, the databases will all be updated with current information.
I assume this would affect anyone still using Windows Vista as well as Windows 7. The rest of you have little to concern yourselves with regarding this problem.
Kirk
NOT GOOD! You should at least be able to run the program from that type of account without jumping through hoops. So I quickly traced the issue to the MANIFEST. You programmers out there know about this. In it were commands asking for higher privileges than we really need, so I think we are going to have a new minor, minor revision on Thursday. Beside fixing that little problem, the databases will all be updated with current information.
I assume this would affect anyone still using Windows Vista as well as Windows 7. The rest of you have little to concern yourselves with regarding this problem.
Kirk
Labels:
manifest,
NetScanTools Pro,
new release,
Windows 7,
Windows Vista
November Newsletter Published
Yesterday I posted our November Newsletter. Key topics center around NetScanTools Pro version 11.
In case you missed it, our first IPv6 capable tools are making their appearance in this new release of NetScanTools Pro and there is even a new WIFI/WLAN/wireless tool.
Something else we talk about is using NetScanTools Pro on an Apple Mac - find out how.
http://www.netscantools.com/newsletters.html
In case you missed it, our first IPv6 capable tools are making their appearance in this new release of NetScanTools Pro and there is even a new WIFI/WLAN/wireless tool.
Something else we talk about is using NetScanTools Pro on an Apple Mac - find out how.
http://www.netscantools.com/newsletters.html
Monday, November 15, 2010
looking at top level domains
Here is a cool thing you can do with NetScanTools Pro. Have you ever needed to look at a top level domain to see name servers or SOA records? It's actually pretty simple and can have some pretty spectacular results.
The other day I wanted to look at the 'bs' domain - really, no kidding. I went to DNS Tools - Core, then entered 'bs.' (the trailing period is REQUIRED), set the name server and set the record type to ANY and pressed NSLOOKUP. Here is what I got back:
[Start Query]
NSLOOKUP Starting Timestamp: 11/15/10 22:35:06
Command line equivalent: "nslookup -recurse -vc -type=ANY bs."
Looking up [bs.]
DNS Name: 4.2.2.2
IP Address: 4.2.2.2
Non-authoritative answer:
bs SOA
SOA origin = DNS.NIC.bs
mail addr = BSADMIN.COB.EDU.bs
serial = 2010111200
refresh = 7200 (2 hours)
retry = 3600 (1 hour)
expire = 3600000 (41 days 16 hours)
min ttl = 86400 (1 day)
bs RRSIG
TTL = 42797 (11 hours 53 mins 17 secs)
NSEC (Next Secure)
Labels = 1
Original TTL = 86400 (1 day)
Signature Expiration = Sun Nov 21 16:00:00 2010
Time Signed = Sun Nov 14 15:00:00 2010
Key Tag = 40288
Signer's Name:
Signature Length: 128 bytes
Signature:
54 0D 4E 76 3B B5 59 45 74 15 AF B1 6F 9A D1 5B
ED FD 19 8A 78 6A D7 70 D5 C9 91 8B 2D 70 B1 E3
21 6D CA 08 A0 28 CF CC 93 63 91 92 FA EC 57 E3
2C 3C DB F9 DD F9 43 2B 90 C6 65 64 7F A0 D3 CA
6B 26 4C 7C 7D 24 1E FE D1 2B 5A F4 17 62 39 C6
C4 AD 2E 37 DD D0 AC 3C E8 53 43 89 AF F3 6D 14
98 F8 DC 1C EC DC 4E 24 B9 8A 2E 06 6E 92 75 F8
18 6E DD 12 63 0E 9D 2D 0A B7 94 3E AF 1D CF 96
bs NSEC
TTL = 42797 (11 hours 53 mins 17 secs)
Next Domain Name: bt
RR Types in Bitmap: NS RRSIG NSEC
bs NS nameserver = DNS.NIC.bs
bs NS nameserver = ANYNS.PCH.NET
bs NS nameserver = UPR1.UPR.CLU.EDU
Server Response Time = 0.233 seconds
[End Query]
As you can see I got back the SOA record, the list of authoritative name servers and the security signature records. Notice how for a top level domain, the authoritative server has mirrors around the world, not just in Bahamas. In fact, there are only three mirrors showing - most top level domains have a lot more than that - the UK has 11. Notice also the domain security record - since last May most top level domains have those records in order to ensure the accuracy of the root data.
You can use the NSLOOKUP tool to inspect the records for any top level domain by following the procedure I outlined above.
The other day I wanted to look at the 'bs' domain - really, no kidding. I went to DNS Tools - Core, then entered 'bs.' (the trailing period is REQUIRED), set the name server and set the record type to ANY and pressed NSLOOKUP. Here is what I got back:
[Start Query]
NSLOOKUP Starting Timestamp: 11/15/10 22:35:06
Command line equivalent: "nslookup -recurse -vc -type=ANY bs."
Looking up [bs.]
DNS Name: 4.2.2.2
IP Address: 4.2.2.2
Non-authoritative answer:
bs SOA
SOA origin = DNS.NIC.bs
mail addr = BSADMIN.COB.EDU.bs
serial = 2010111200
refresh = 7200 (2 hours)
retry = 3600 (1 hour)
expire = 3600000 (41 days 16 hours)
min ttl = 86400 (1 day)
bs RRSIG
TTL = 42797 (11 hours 53 mins 17 secs)
NSEC (Next Secure)
Labels = 1
Original TTL = 86400 (1 day)
Signature Expiration = Sun Nov 21 16:00:00 2010
Time Signed = Sun Nov 14 15:00:00 2010
Key Tag = 40288
Signer's Name:
Signature Length: 128 bytes
Signature:
54 0D 4E 76 3B B5 59 45 74 15 AF B1 6F 9A D1 5B
ED FD 19 8A 78 6A D7 70 D5 C9 91 8B 2D 70 B1 E3
21 6D CA 08 A0 28 CF CC 93 63 91 92 FA EC 57 E3
2C 3C DB F9 DD F9 43 2B 90 C6 65 64 7F A0 D3 CA
6B 26 4C 7C 7D 24 1E FE D1 2B 5A F4 17 62 39 C6
C4 AD 2E 37 DD D0 AC 3C E8 53 43 89 AF F3 6D 14
98 F8 DC 1C EC DC 4E 24 B9 8A 2E 06 6E 92 75 F8
18 6E DD 12 63 0E 9D 2D 0A B7 94 3E AF 1D CF 96
bs NSEC
TTL = 42797 (11 hours 53 mins 17 secs)
Next Domain Name: bt
RR Types in Bitmap: NS RRSIG NSEC
bs NS nameserver = DNS.NIC.bs
bs NS nameserver = ANYNS.PCH.NET
bs NS nameserver = UPR1.UPR.CLU.EDU
Server Response Time = 0.233 seconds
[End Query]
As you can see I got back the SOA record, the list of authoritative name servers and the security signature records. Notice how for a top level domain, the authoritative server has mirrors around the world, not just in Bahamas. In fact, there are only three mirrors showing - most top level domains have a lot more than that - the UK has 11. Notice also the domain security record - since last May most top level domains have those records in order to ensure the accuracy of the root data.
You can use the NSLOOKUP tool to inspect the records for any top level domain by following the procedure I outlined above.
Friday, November 5, 2010
NetScanTools Pro 11 status
Another week has passed. This week included quite a bit of work on version 11 - again in the area of IPv6. NSLOOKUP and Dig both now accept IPv6 address inputs.
Most importantly, whois now accepts IPv6 inputs. Whois' ip to hostname to ip now work with IPv6. So if you enter a domain name, it will check for both IPv4 and IPv6 addresses. Plus, the whois servers for showing ownership or delegation of the IPv6 addresses are now in the database and it will make the correct query based on the input IPv6 address.
A few more new things next week and then wrap up for release.
Kirk
Most importantly, whois now accepts IPv6 inputs. Whois' ip to hostname to ip now work with IPv6. So if you enter a domain name, it will check for both IPv4 and IPv6 addresses. Plus, the whois servers for showing ownership or delegation of the IPv6 addresses are now in the database and it will make the correct query based on the input IPv6 address.
A few more new things next week and then wrap up for release.
Kirk
Labels:
DNS Tools,
IPv4,
IPv6,
NetScanTools Pro,
whois
Friday, October 29, 2010
IPv6 Tools in NetScanTools Pro v11
NetScanTools Pro v11 will have the first real IPv6 tools that we have done ever in it. The ability to retrieve DNS AAAA records has always been there, but we've gone beyond that. Here are a sample of the completed tools.
DNS Tools - Basic now includes a Simple Query - IPv6 tool. This tool accepts a hostname like ipv6.google.com or a IPv6 Address like 2001:6b0:1:ea:202:a3ff:fecd:23a7 and attempts to retrieve the IPv6 address or hostname respectively.
DNS Tools - Advanced now includes an IP/Hostname to ASN tool that accepts either a hostname or an IPv4/IPv6 address and returns the ASN.
Ping - Enhanced now includes an ICMPv6 mode.
More IPv6 to come next week. Think about NetScanTools Pro v11 when you need some GUI IPv6 tools. NetScanTools Pro v11 will be released in November. We're getting closer!
DNS Tools - Basic now includes a Simple Query - IPv6 tool. This tool accepts a hostname like ipv6.google.com or a IPv6 Address like 2001:6b0:1:ea:202:a3ff:fecd:23a7 and attempts to retrieve the IPv6 address or hostname respectively.
DNS Tools - Advanced now includes an IP/Hostname to ASN tool that accepts either a hostname or an IPv4/IPv6 address and returns the ASN.
Ping - Enhanced now includes an ICMPv6 mode.
More IPv6 to come next week. Think about NetScanTools Pro v11 when you need some GUI IPv6 tools. NetScanTools Pro v11 will be released in November. We're getting closer!
Wednesday, October 27, 2010
NetScanTools LE Finalist in 2010 Innovation Awards
NetScanTools LE was named a Finalist in the software category for the Officer.com 2010 Innovation Awards. Our thanks go to Cygnus Business Media's Law Enforcement Group for the honor.
Please read this news story on Officer.com detailing the Awards.
About NetScanTools LE.
NetScanTools® LE (Law Enforcement) is an Internet Information collection software tool for Windows that gives you information and reports about an IP Address, Hostname, Domain Name, Email Address or URL (web address). It was designed especially for Law Enforcement.
Current NetScanTools LE version is 1.31.
Read more about NetScanTools LE and download a free 30 day trial.
Please read this news story on Officer.com detailing the Awards.
About NetScanTools LE.
NetScanTools® LE (Law Enforcement) is an Internet Information collection software tool for Windows that gives you information and reports about an IP Address, Hostname, Domain Name, Email Address or URL (web address). It was designed especially for Law Enforcement.
Current NetScanTools LE version is 1.31.
Read more about NetScanTools LE and download a free 30 day trial.
Tuesday, October 26, 2010
IPv6 and DNS Tools
NetScanTools Pro v11 Status as of today.
Working on IPv6 additions to NetScanTools Pro v11. We now have two new IPv6 capable DNS tools. I should have the other DNS tools I'm adding complete in the next day or so. Then I will add one or two more IPv6 tools soon after.
Kirk
Working on IPv6 additions to NetScanTools Pro v11. We now have two new IPv6 capable DNS tools. I should have the other DNS tools I'm adding complete in the next day or so. Then I will add one or two more IPv6 tools soon after.
Kirk
Wednesday, October 20, 2010
October Newsletter Published
Unlike last month's newsletter, this one is on time. There are quite a few new topics including a mention of that Cisco Small Business Switch review. Status updates on NetScanTools Pro v11 are in it too.
The October NetScanTools Newsletter can be read here:
http://www.netscantools.com/newsletters.html
The October NetScanTools Newsletter can be read here:
http://www.netscantools.com/newsletters.html
New NetScanTools Pro v11 Screenshots Posted
Today I posted quite a few new screenshots of NetScanTools Pro v11. They are on Facebook:
http://www.facebook.com/album.php?aid=35226&l=be83320aaf&id=117859474900452
Back to work...
Kirk
http://www.facebook.com/album.php?aid=35226&l=be83320aaf&id=117859474900452
Back to work...
Kirk
Friday, October 15, 2010
Week Recap
It's been another busy week. Here is what was accomplished.
SNMP tools are all complete - new things in SNMP: SNMPv3, getnext, more bulk tools. SNMP has been split into basic tools and advanced or specialized tools. This was the last tool to be transferred from the old v10 interface to the new v11 interface.
Ping Scan (or Ping Sweep AKA NetScanner) has been 98% completed. This has several improvements such as columns that appear or disappear based on whether the scan option is active. The last 2% to complete has to do with automatic transfer of IP/MAC address pairs to the IP/MAC database - forgot this part until this evening.
Port Scan was rewritten completely for NetScanTools LE, so that is the basis of the Pro version port scanner. I still have to put the TCP stealth scanning modes into it. Those were being worked on today.
After those things are complete, it's time for folding in a few new tools. Then on to cleanup, documentation changes and release. It's getting close!
Kirk
ps. don't forget to follow us on twitter @netscantools or on Facebook (link is on the netscantools.com main page)
SNMP tools are all complete - new things in SNMP: SNMPv3, getnext, more bulk tools. SNMP has been split into basic tools and advanced or specialized tools. This was the last tool to be transferred from the old v10 interface to the new v11 interface.
Ping Scan (or Ping Sweep AKA NetScanner) has been 98% completed. This has several improvements such as columns that appear or disappear based on whether the scan option is active. The last 2% to complete has to do with automatic transfer of IP/MAC address pairs to the IP/MAC database - forgot this part until this evening.
Port Scan was rewritten completely for NetScanTools LE, so that is the basis of the Pro version port scanner. I still have to put the TCP stealth scanning modes into it. Those were being worked on today.
After those things are complete, it's time for folding in a few new tools. Then on to cleanup, documentation changes and release. It's getting close!
Kirk
ps. don't forget to follow us on twitter @netscantools or on Facebook (link is on the netscantools.com main page)
Thursday, October 7, 2010
NetScanTools LE 1.31 Released October 7, 2010
Yes, we've been busy this week. Some of the same changes made to NetScanTools Pro were rolled into NetScanTools LE. They relate to the DNS issues. We also updated the whois and ip to country databases. If you already have NetScanTools LE, download the install file and install over the top of the older version.
Back to NetScanTools Pro version 11...
Back to NetScanTools Pro version 11...
Wednesday, October 6, 2010
NetScanTools (TM) Pro 10.98 Published
On Monday, October 4, we released NetScanTools Pro 10.98 installed version. The USB version patch was released on Tuesday, October 5.
Here are the changes:
- Ping will now allow up to 8192 consecutive pings to sent. Problems occurred in the previous version if you exceeded 256 pings as defined in Setup.
- Certain DNS functions that use the secondary resolver (ex. Get Basic DNS Records) will now properly handle the truncated flag in the UDP response that indicates the query should be retried using TCP.
- DNS Tools - Core: Fixed problem where if a very large response to a single record query was obtained, all the records would be displayed. Example would be a large PTR record response for a single IP address.
- Updated SQLite to version 3.7.2.
- Updated database files. Removed whois prefix files.
Wednesday, September 29, 2010
Review of the Cisco SF 300-08 Small Business Switch

Yesterday I received the first new switch for our stable of test switches in a couple years. It's on of a brand new series from Cisco that was just announced last week called the Cisco Small Business 300 Series Managed Switches, and I'll have to say - I'm impressed.
I opened the box and found all the hardware I needed to either rack mount it, mount it on a wall or table and a 'wall wart' style AC adapter power supply. The first thing I noticed about the AC adapter was that it was narrow and had the AC prongs turned 90 degrees from usual - this allowed me to drop it right into a standard power strip without wasting two or more places in the power strip. I did thumb through the Quick Start Guide to get the login info and learn about the configuration.
So after powering down most of the computers, I put the new SF 300-08 8 port switch into our network. I'm replacing (sort-of) a workhorse HP Procurve 2524 with this Cisco switch because it uses less power and is less noisy - no fans - I really only use 7 ports on a daily basis. The older switch is still there for testing and expansion when needed.
As soon as I put it in, the switch used DHCP to get a network address from our server. This was handy, but I will be changing it to a static IP later. The fact that it can use DHCP is a very nice feature because this means you don't have to connect the included serial port cable or take a laptop and change the laptop IP/mask to match the factory defaults.
The next thing I need to do was test it with our Managed Switch Port Mapping Tool. A quick check with the tool determined that SNMP is not active out of the box. So using IE8, I logged in with the default credentials that I found in the Quick Start Guide and the first thing it asked me to do was change the password. Right away I was presented with a change password window complete with a Password Strength meter that shows the strength in red-yellow-green. After getting past that point, the web based interface was clean and well organized, in fact much better organized than I expected. The web interface can best be described as 'outlook' style with a control panel on the left and user interaction windows on the right.
I also found it easy to set the switch time clock by having it get the time from the computer from the Administration controls. I could have also selected SNTP options.
Since the Managed Switch Port Mapping Tool uses SNMPv1 or v2c (v3 coming soon), I had to enable SNMP. I found that to do this, I had to change settings in two places. The first was to enable SNMP, this is done on the Security - TCP/UDP Services window. Next I had to create access to the OID data by creating an SNMPv1/v2c 'community' associated with a 'view'. The default 'View' gives you access to the whole .1 OID structure, so that's the one I chose. There are many other options for excluding portions of the OID tree depending on the 'view'. Essentially what I chose amounts to allowing full read access via SNMP v1/v2c for my computer's specific IP address (SNMP Management Station). once those settings were in place, I was able to run the Managed Switch Port Mapping Tool.
Right away I had the results I expected to see. The list of 8 ethernet ports with MAC addressess and IP addresses. The duplex mode info showed up (always an issue since standardization eludes switch manufacturers) and the Spanning Tree Protocol info was there and appeared correct. There are two things I need to look into: First, every port that had a MAC address had a VLAN 1 entry as I would expect, but what I didn't expect to see was a second VLAN '0' not associated with any MAC address below it. I'll have to find out where that is coming from. It does not seem to affect quality of the results. The second issue is that the physical ports are called e1-e8 and there are a second set of ports ch1-ch8 that are also labeled as ethernet. They are disabled and have an ifIndex beginning with 1000. The e1-8 ports are ifIndex 1 through 8. I also noted that BRIDGE-MIB::dot1dBaseNumPorts.0 = 16 which means the software probably supports the 16 port version even though this is an 8 port device. Just an interesting observation.
It appears that the SNMP implementation of this device is a departure from other Cisco switches in that 'community name indexing' is not supported. This has been historically used in Cisco switches to obtain the Bridge Mib information on a per VLAN basis. This does not affect our results since the device appears to fully support Q-Bridge Mib and that gives us access to VLAN specific port assignments.
Here is a screenshot of the Switch Port Mapping Tool results for this switch.

Bottom Line: This is a very powerful switch for the money. I've barely scratched the surface with its capabilities. There is direct support for IPv6, QOS settings, access lists by IP or MAC address, logging and actually far more than I expected for under $200. I used the help system and found that it was very readable and clear unlike much online help you find today. I highly recommend this switch series based on what I've seen so far.
Reviewed with switch firmware version 1.0.0.27.
Tuesday, September 28, 2010
September Newsletter Published
Yes, I know it's October on Friday, but I've been busy. The September NetScanTools Newsletter can be read here:
http://www.netscantools.com/newsletters.html
Follow the progress of NetScanTools Pro v11 on Twitter or on Facebook.
http://www.netscantools.com/newsletters.html
Follow the progress of NetScanTools Pro v11 on Twitter or on Facebook.
Friday, September 24, 2010
Week Recap
It's been a busy week. I spent alot of time dealing with CRT issues moving the SNMP tool set into NetScanTools Pro 11. The final set of SNMP tools will be put in there today, then I have to finish up a few tools that were left unfinished.
Yesterday I ordered a new Cisco 300 Series Managed Switch from Newegg to see how it performs with the Managed Switch Port Mapping Tool. This is a new series of switch that Cisco announced on Wednesday. The documentation says that it supports SNMP v1, 2c and 3, so I want to see if it can be mapped from the switch port mapper. I should be getting it on Tuesday, so I'll replace an old Linksys Etherfast 4116 with it, then we'll see what happens. I'm curious to know if the SNMP implementation follows the Cisco codebase or is a continuation of the old Linksys code. I guess I'll find out.
I'm also looking for boxshot software - I don't know which is the best, so I'll take any comments.
Yesterday I ordered a new Cisco 300 Series Managed Switch from Newegg to see how it performs with the Managed Switch Port Mapping Tool. This is a new series of switch that Cisco announced on Wednesday. The documentation says that it supports SNMP v1, 2c and 3, so I want to see if it can be mapped from the switch port mapper. I should be getting it on Tuesday, so I'll replace an old Linksys Etherfast 4116 with it, then we'll see what happens. I'm curious to know if the SNMP implementation follows the Cisco codebase or is a continuation of the old Linksys code. I guess I'll find out.
I'm also looking for boxshot software - I don't know which is the best, so I'll take any comments.
Tuesday, September 21, 2010
Managed Switch Port Mapping Tool v1.99.1 Released
I have not said much about this tool in this blog. Here is a brief synopsis. Network Switches come in generally two flavors: managed and unmanaged. Managed Switches have an IP address and can have all kinds of internal parameters monitored and changed, as opposed to unmanaged switches that simply they do what they do without any user control.
Managed Switches usually have more than one way to manage them, the most common being a web interface, followed by SNMP v1, v2c and sometimes v3, CLI through telnet and finally a console connector on the front or back. Our tool uses SNMP v1 or v2c to communicate with the switch (or switches). [we will be adding support for SNMP v3 in the next major release of the program]
What it does: The Managed Switch Port Mapping Tools talks with the switch and 'maps' or analyzes the information to remotely find out the mac addresses of devices attached to the physical ports. It also attempts to find the IPv4 addresses that match the mac addresses and shows you many other parameters from the switch.
This tool is very useful to network technicians who must figure out what devices are attached to switch ports.
This new release fixes a few problems and enhances the speed and ability to map switches. You can read about it two places:
http://www.switchportmapper.com/
or
http://www.netscantools.com/spmapmain.html
Download a 30 day trial copy today from either site.
Managed Switches usually have more than one way to manage them, the most common being a web interface, followed by SNMP v1, v2c and sometimes v3, CLI through telnet and finally a console connector on the front or back. Our tool uses SNMP v1 or v2c to communicate with the switch (or switches). [we will be adding support for SNMP v3 in the next major release of the program]
What it does: The Managed Switch Port Mapping Tools talks with the switch and 'maps' or analyzes the information to remotely find out the mac addresses of devices attached to the physical ports. It also attempts to find the IPv4 addresses that match the mac addresses and shows you many other parameters from the switch.
This tool is very useful to network technicians who must figure out what devices are attached to switch ports.
This new release fixes a few problems and enhances the speed and ability to map switches. You can read about it two places:
http://www.switchportmapper.com/
or
http://www.netscantools.com/spmapmain.html
Download a 30 day trial copy today from either site.
Tuesday, September 14, 2010
XBox 360 Slim Wireless MAC Address Problem?
Last night at midnight my son bought Halo Reach and the new XBox 360 Slim. When I got up he told me he couldn't connect to the wireless router. The first thing I did was check his XBox wireless settings which looked OK. Then I had him note down the XBox wireless MAC address from advanced settings - while he did that I noticed that the 'Wired MAC address' was significantly different.
Then we went to the router and checked the MAC he had entered in the list of authorized MACs in the MAC Filtering list. Fine - he typed it in right. Then I had him view the router logs. I saw right away that the MAC address that the XBox was trying to connect with was not the 'wireless' MAC address - it was the Wired MAC address. He change the router filter MAC list to match the Wired MAC address - problem solved.
Seems like an OOPS! Hope this helps someone.
Kirk
Then we went to the router and checked the MAC he had entered in the list of authorized MACs in the MAC Filtering list. Fine - he typed it in right. Then I had him view the router logs. I saw right away that the MAC address that the XBox was trying to connect with was not the 'wireless' MAC address - it was the Wired MAC address. He change the router filter MAC list to match the Wired MAC address - problem solved.
Seems like an OOPS! Hope this helps someone.
Kirk
Labels:
connection problem,
Halo,
MAC Address problem,
mac filtering,
wireless router,
Xbox,
XBox 360 Slim
Thursday, September 9, 2010
Podcast with Keith Parsons wirelesslanprofessionals.com
On September 7th, Keith Parsons of wirelesslanprofessionals.com interviewed Kirk Thomas about NetScanTools Pro and how it can be used by wireless LAN professionals. We covered a wide range of topics including using the Managed Switch Port Mapping tool and we even touched on NetScanTools LE. Keith operates almost entirely in a free roaming wireless world and focusses on the Wireless Lan aspects of life. He teaches classes, is a consultant and is an authority on wireless networking.
Now that I have your interest, please check out: wirelesslanprofessionals.com
If you blink, you might miss the 40% discounts for NetScanTools Pro and the Managed Switch Port Mapping tool that are talked about on that page. Go listen to the podcast today!
Kirk
Now that I have your interest, please check out: wirelesslanprofessionals.com
If you blink, you might miss the 40% discounts for NetScanTools Pro and the Managed Switch Port Mapping tool that are talked about on that page. Go listen to the podcast today!
Kirk
Thursday, September 2, 2010
NetScanTools LE Reviewed Aug 31, 2010
Kevin Beaver of 'Hacking for Dummies' and other 'for Dummies' books fame wrote an excellent review of NetScanTools LE on August 31. Please check it out here on his blog:
http://securityonwheels.blogspot.com/2010/08/netscan-tools-le-must-have-for.html
Thanks Kevin!
http://securityonwheels.blogspot.com/2010/08/netscan-tools-le-must-have-for.html
Thanks Kevin!
NetScanTools LE 1.30 Released Sept 1, 2010
Yesterday we released NetScanTools LE 1.30. This new release has many minor fixes and at least one fairly major bug fix: if you were using Automated tools and entered a long domain name AND had 'IP to Country' checked, it would shut down when it got to the IP/Country section. This problem has been fixed. We also did a lot of minor user interface fixes. We also updated WinPcap to 4.1.2 and SQLite to 3.7.2. As usual we updated the whois server and IP to Country databases.
If you already have NetScanTools LE 1.2 or earlier, simply start it, look for the notice that a new version is available and follow the instructions. If you have a purchased copy, it will find your keys. If you have a trial copy, you will get a new 30 day trial.
If you already have NetScanTools LE 1.2 or earlier, simply start it, look for the notice that a new version is available and follow the instructions. If you have a purchased copy, it will find your keys. If you have a trial copy, you will get a new 30 day trial.
Tuesday, August 31, 2010
New Packet Generator Features
NetScanTools Pro v11 will have a new ARP packet generator that gives you full control over all the contents of the fields in an IPv4 ARP packet. We've also added a new hex editor tool so that you can create or change the content of payload files that you add to TCP or UDP packets.
Version 11 is not released yet, but that's a quick preview of some of the new things in the upcoming release.
Version 11 is not released yet, but that's a quick preview of some of the new things in the upcoming release.
Labels:
ARP,
hex editor,
NetScanTools Pro,
packet generator
Tuesday, August 3, 2010
FireFox slowed my old computer one too many times
Yesterday I had a meeting with a client and I was late because one of my old computers (XP Pro) had slowed down way too much. All I was running was an email client (not outlook) and Firefox 3.6.8. Firefox had a been running for a few hours as I visited some websites. I couldn't bring up Task Manager or get the windows to repaint. I had to wait and wait while I tried to kill Firefox. Once I got it killed everything worked normally. This has happened several times lately - usually after visiting Facebook, then moving on elsewhere. FYI, NetScanTools is on Facebook you know.
So I did a bit of searching and found an article that explained about a new feature called plugin-container.exe. If you disable it, things appear to work better.
It's pretty simple to disable the plugin container.
Start Firefox.
Enter about:config into the browser and press Enter.
Press the scary warning button.
Look for the items beginning with dom.ipc - six will be listed, you want the middle four.
Double click on each of those four to change them from TRUE to FALSE.
Restart Firefox.
At least for me the problems of memory usage and processor time disappeared. Hopefully permanently and I hope that the Firefox developers know about this and can fix it.
If you want to see the article I found, go here:
http://www.technogadge.com/how-to-stop-firefox-plugin-container-exe-process/
So I did a bit of searching and found an article that explained about a new feature called plugin-container.exe. If you disable it, things appear to work better.
It's pretty simple to disable the plugin container.
Start Firefox.
Enter about:config into the browser and press Enter.
Press the scary warning button.
Look for the items beginning with dom.ipc - six will be listed, you want the middle four.
Double click on each of those four to change them from TRUE to FALSE.
Restart Firefox.
At least for me the problems of memory usage and processor time disappeared. Hopefully permanently and I hope that the Firefox developers know about this and can fix it.
If you want to see the article I found, go here:
http://www.technogadge.com/how-to-stop-firefox-plugin-container-exe-process/
Thursday, July 29, 2010
PHPList problem solved - send message page blank
Well I wasted over 2 hours fixing PHPList - again. A couple of days ago I upgraded from 2.10.10 to 2.10.12. Today I was in a hurry to get a newsletter out before the end of the 'east coast' day. I wrote it, then went to phplist and tried to 'send a message'. I got there and found all the tabs like content etc visible, but NO editor. Apparently there was a problem with the FCKEditor. I spent a long time going through the support forums - a long time. I looked at the .tgz backup and discovered that when I first installed PHPList I had to modify config.php and send_core.php - it had to be in those. I tried several things including switching editors in the config, but none worked.
I finally ran across a forum topic called "Send a message screen: nothing under the tabs" that gave me the solution and the real cause of the problem: "If you are running v2.10.11 or v2.10.12, one possible cause for this issue is that your PHP installation doesn't include the iconv module. You can check this by looking at your system details: lists/admin/?page=community"
I was missing the iconv module in the list of loaded php modules.
So apparently the solution is to comment out the calls that access iconv in send_core.php. I had messed with this file in 2.10.10 but I couldn't remember the changes I made. So I commented out the lines (using #) beginning at 1032 as follows:
# $utf8_subject = $subject;
# $utf8_from = $from;
# if (strcasecmp($GLOBALS['strCharSet'], 'utf-8') <> 0) {
# $utf8_subject = iconv($GLOBALS['strCharSet'],'UTF-8',$utf8_subject);
# $utf8_from = iconv($GLOBALS['strCharSet'],'UTF-8',$utf8_from);
# }
Problem solved. Now I've put this in the blog so the next time I upgrade PHPList, I'll remember. And this might also help someone else too.
I finally ran across a forum topic called "Send a message screen: nothing under the tabs" that gave me the solution and the real cause of the problem: "If you are running v2.10.11 or v2.10.12, one possible cause for this issue is that your PHP installation doesn't include the iconv module. You can check this by looking at your system details: lists/admin/?page=community"
I was missing the iconv module in the list of loaded php modules.
So apparently the solution is to comment out the calls that access iconv in send_core.php. I had messed with this file in 2.10.10 but I couldn't remember the changes I made. So I commented out the lines (using #) beginning at 1032 as follows:
# $utf8_subject = $subject;
# $utf8_from = $from;
# if (strcasecmp($GLOBALS['strCharSet'], 'utf-8') <> 0) {
# $utf8_subject = iconv($GLOBALS['strCharSet'],'UTF-8',$utf8_subject);
# $utf8_from = iconv($GLOBALS['strCharSet'],'UTF-8',$utf8_from);
# }
Problem solved. Now I've put this in the blog so the next time I upgrade PHPList, I'll remember. And this might also help someone else too.
Tuesday, June 29, 2010
NetScanTools® Pro 10.97 USB Patch Published
Today we finished and posted the USB version patch. If your maintenance plan is active you can login through Help/Check for New Version and get the patch. The changes are the same as in the installed version.
Monday, June 28, 2010
What is NetScanTools?
Let's start with a little history. Back in 1995 - the dawn of the public's awareness of the internet when the World Wide Web was still in it's infancy, there were very few network enabled applications for Windows 95 or Windows NT 3.5. Many of those tools that were out there were simple one function tools. A couple that I specifically remember were WS_PING and WS_FTP written by John A. Junod. I still have a very old functioning copy of WS_FTP. Those tools were eventually marketed by Ipswitch.
Junod's tools, along with others inspired me to combine several tools together in a convenient package rather than having multiple programs each doing a single task. Because I thought networking, specifically the internet, was the direction things were going, I decided to put together a simple DNS lookup tool (IP address to hostname and vice versa) called Get Host Name, Finger and Socket Info and make it work in Windows. (Remember that in 1995 Unix, BSD, Solaris etc, completely ruled the networking roost. Windows and networking were mutually exclusive ideas to Unix experts - they chuckled at the thought of even seeing a Windows machine on a network.) NetScanTools was compiled using Visual C++ 1(?) - a 16 bit version. I quickly wrote the program simply to boost sales of a long since dead duplicate file location utility called SystemScanTools. Since my new tool worked on a network, I called it NetScanTools. Here is a picture of the v1.10. Believe it or not it still works - I took this picture today.

See the tabbed interface? It's something I think I used before anyone else as the basis of this type of multifunction tool application. This type of interface is still popular with some of long time customers because you can run more than one tool simultaneously. Unfortunately our current 'Outlook' style interface didn't allow more than one tool at a time. But in NetScanTools Pro version 11 we are bringing back the ability to run more than one tool simultaneously.
One thing lead to another and NetScanTools got popular. Really popular. So popular that we were doing 3 GB transfer of downloads a day - we had to have multiple download sites. In 1998, we decided it was time for a more advanced 'Pro' version. So in July 1999 NetScanTools Pro 1.0 was released. We continued on with NetScanTools Standard as it was now known until August 2004.
Fast forward to now. I'm working hard on NetScanTools Pro version 11. It will have an updated 'Outlook' style interface with a Favorites left panel group and it supports simultaneous tool operation. Plus it has the ability to automatically save all results to a database. Just like NetScanTools LE (Law Enforcement) version. The program is being refocussed to make it very clear what each tool does and to separate the tools into more logical functions.
What is NetScanTools? Quite simply, NetScanTools brings together a wide variety of networking tools into one easy to use package on a Windows 7/Vista/XP/2008/2003/2000 environment. The tools range from simple tools like NTP Time Sync to complex ARP tools and even more complex DNS tools.
So who needs NetScanTools Pro? Lots of people. It's primarily useful to network engineers or network technicians because it puts many tools they need in one place. The tools range from specialized DNS tools to ping sweep, arp sweep, packet generation, packet capture and a fairly complicated whois tool. Much of what is in there was added as a result of customer feedback. Although it has been historically IPv4, I am going to be putting more IPv6 functions in it because that's where the future is.
Why should you pay for something that you can get for free? Good question. I've looked at quite a few of those free Windows based network tool apps. The ease of use is often not there. The freeware ones simply don't always function as advertised, and some that are advertised as free are not really free - many of the coolest functions on that not-really-free popular app stop working after X days. And as is the case with most freeware, development goes along for a few years then suddenly stops. I've seen it happen to several apps. But we are still here. If you need to call and ask a question, I'll talk to you. If you need to email, I'll email back (please whitelist netscantools.com or you may not get a response - personal rant against those blasted overzealous spam filters). So thanks to all those who have supported us over all these years. We hope to continue providing this tool for a few more years.
Junod's tools, along with others inspired me to combine several tools together in a convenient package rather than having multiple programs each doing a single task. Because I thought networking, specifically the internet, was the direction things were going, I decided to put together a simple DNS lookup tool (IP address to hostname and vice versa) called Get Host Name, Finger and Socket Info and make it work in Windows. (Remember that in 1995 Unix, BSD, Solaris etc, completely ruled the networking roost. Windows and networking were mutually exclusive ideas to Unix experts - they chuckled at the thought of even seeing a Windows machine on a network.) NetScanTools was compiled using Visual C++ 1(?) - a 16 bit version. I quickly wrote the program simply to boost sales of a long since dead duplicate file location utility called SystemScanTools. Since my new tool worked on a network, I called it NetScanTools. Here is a picture of the v1.10. Believe it or not it still works - I took this picture today.

See the tabbed interface? It's something I think I used before anyone else as the basis of this type of multifunction tool application. This type of interface is still popular with some of long time customers because you can run more than one tool simultaneously. Unfortunately our current 'Outlook' style interface didn't allow more than one tool at a time. But in NetScanTools Pro version 11 we are bringing back the ability to run more than one tool simultaneously.
One thing lead to another and NetScanTools got popular. Really popular. So popular that we were doing 3 GB transfer of downloads a day - we had to have multiple download sites. In 1998, we decided it was time for a more advanced 'Pro' version. So in July 1999 NetScanTools Pro 1.0 was released. We continued on with NetScanTools Standard as it was now known until August 2004.
Fast forward to now. I'm working hard on NetScanTools Pro version 11. It will have an updated 'Outlook' style interface with a Favorites left panel group and it supports simultaneous tool operation. Plus it has the ability to automatically save all results to a database. Just like NetScanTools LE (Law Enforcement) version. The program is being refocussed to make it very clear what each tool does and to separate the tools into more logical functions.
What is NetScanTools? Quite simply, NetScanTools brings together a wide variety of networking tools into one easy to use package on a Windows 7/Vista/XP/2008/2003/2000 environment. The tools range from simple tools like NTP Time Sync to complex ARP tools and even more complex DNS tools.
So who needs NetScanTools Pro? Lots of people. It's primarily useful to network engineers or network technicians because it puts many tools they need in one place. The tools range from specialized DNS tools to ping sweep, arp sweep, packet generation, packet capture and a fairly complicated whois tool. Much of what is in there was added as a result of customer feedback. Although it has been historically IPv4, I am going to be putting more IPv6 functions in it because that's where the future is.
Why should you pay for something that you can get for free? Good question. I've looked at quite a few of those free Windows based network tool apps. The ease of use is often not there. The freeware ones simply don't always function as advertised, and some that are advertised as free are not really free - many of the coolest functions on that not-really-free popular app stop working after X days. And as is the case with most freeware, development goes along for a few years then suddenly stops. I've seen it happen to several apps. But we are still here. If you need to call and ask a question, I'll talk to you. If you need to email, I'll email back (please whitelist netscantools.com or you may not get a response - personal rant against those blasted overzealous spam filters). So thanks to all those who have supported us over all these years. We hope to continue providing this tool for a few more years.
NetScanTools® Pro 10.97 Published
Today we posted NetScanTools Pro 10.97. This is the 'installed' version, the USB version will be ready on Tuesday if all goes well. It has a few fixes like changes to the NetBIOS Basic tool (it's not really using NetBIOS anymore, it really uses SMB/CIFS) and a fix to the TCP connection stopping function in Network Stats. There are the usual database updates.
Work on version 11 is going well.
Work on version 11 is going well.
Wednesday, June 23, 2010
June Newsletter Published
You can see our latest June NetScanTools newsletter here.
Tuesday, June 8, 2010
Renaming tools for NetScanTools Pro 11
We have renamed some tools in NetScanTools Pro 11:
NetScanner is now Ping Sweep
ARP has been split into Arp Cache and Arp Scan
NetBios Info - Shares/System Basics is now Network Shares
Packet Viewer is now Packet Capture
This will make it more clear to people what the tools are for and what they actually do.
NetScanner is now Ping Sweep
ARP has been split into Arp Cache and Arp Scan
NetBios Info - Shares/System Basics is now Network Shares
Packet Viewer is now Packet Capture
This will make it more clear to people what the tools are for and what they actually do.
Wednesday, June 2, 2010
NetScanTools Pro USB Version Sale
Get NetScanTools Pro 10.96.1 on a portable USB flash drive for $50 off through Friday, June 4, 2010. This version of NetScanTools Pro does not need to be installed on the computer you are using it on. The flash drive is a very fast Ready Boost compatible 4GB drive with plenty of extra space for other things you might want to install on it like the portable version of Wireshark.
Details:
http://www.netscantools.com/
Sale is over.
Details:
http://www.netscantools.com/
Sale is over.
Thursday, May 20, 2010
ipPulse 1.70 released May 20, 2010
I bet you don't know what ipPulse is. So this release announcement may be a shock too. It's the first release in five (5) years and a fairly big one at that.
First of all, what is ipPulse? it is a program designed to cycle through a list of network connected devices and test them one at a time. It can have one or two tests per machine. The first test called the primary test can be either a Ping to see if it responds or a TCP connect to a port of your choice to see if a service is alive on the target. The second optional test can be either a TCP port test (different port) or an SNMP v1/v2c walk of the active interfaces. Failures can be logged and someone can be notified that a failure occurred. Notification can be audible or by email to a computer to a cell phone. That's it. A pretty simple, but effective program. There are programs out there that cost over 10x as much that do pretty much the same thing with more bells and whistles.
So what did we change from the last version of five years ago? For starters it was compiled by the newer Visual Studio 2008 (next time maybe VS2010). Two things were removed: 1. ping using 'raw sockets'. This was redundant because it had another Ping setting. 2. Support for pagers. I haven't seen anyone with a pager in a long time. Cell phones can be emailed from the program (ie. phoneNumber@vtext.com), so unless anyone has a real heart attack over it, pager support is gone. The next thing was Windows 7 (and Vista) support. Previous versions of Windows 'looked the other way' when we wrote our log files and list of targets in the program installation directory. Windows 7 and Vista don't like that at all. So now those writable files go in the user data directory where they belong. The final change was converting from the ancient Wise installer to the latest version of Inno Setup. So now it should run fine on Windows 7, Vista, XP, 2008, 2003 and 2000. Older Windows are not supported - oh well, time to move on.
If you are interested, you can find it at http://www.nwpsw.com/ippulsemain.html
I forgot to mention that it costs $69 for an unlock code. We used to compile a separate CDROM version, but like 45's, CDROMs are vanishing, so now it's just an unlock code. If you have an older version from CDROM and you want to upgrade, contact us for the unlock code. Give us your name, email and CDKEY or invoice number and we'll give you the unlock code for 1.70.
First of all, what is ipPulse? it is a program designed to cycle through a list of network connected devices and test them one at a time. It can have one or two tests per machine. The first test called the primary test can be either a Ping to see if it responds or a TCP connect to a port of your choice to see if a service is alive on the target. The second optional test can be either a TCP port test (different port) or an SNMP v1/v2c walk of the active interfaces. Failures can be logged and someone can be notified that a failure occurred. Notification can be audible or by email to a computer to a cell phone. That's it. A pretty simple, but effective program. There are programs out there that cost over 10x as much that do pretty much the same thing with more bells and whistles.
So what did we change from the last version of five years ago? For starters it was compiled by the newer Visual Studio 2008 (next time maybe VS2010). Two things were removed: 1. ping using 'raw sockets'. This was redundant because it had another Ping setting. 2. Support for pagers. I haven't seen anyone with a pager in a long time. Cell phones can be emailed from the program (ie. phoneNumber@vtext.com), so unless anyone has a real heart attack over it, pager support is gone. The next thing was Windows 7 (and Vista) support. Previous versions of Windows 'looked the other way' when we wrote our log files and list of targets in the program installation directory. Windows 7 and Vista don't like that at all. So now those writable files go in the user data directory where they belong. The final change was converting from the ancient Wise installer to the latest version of Inno Setup. So now it should run fine on Windows 7, Vista, XP, 2008, 2003 and 2000. Older Windows are not supported - oh well, time to move on.
If you are interested, you can find it at http://www.nwpsw.com/ippulsemain.html
I forgot to mention that it costs $69 for an unlock code. We used to compile a separate CDROM version, but like 45's, CDROMs are vanishing, so now it's just an unlock code. If you have an older version from CDROM and you want to upgrade, contact us for the unlock code. Give us your name, email and CDKEY or invoice number and we'll give you the unlock code for 1.70.
Labels:
alerts,
ipPulse,
log files,
new release,
Ping,
TCP connect,
Visual C++ 2008
MSVCR90.DLL problem on XP
File this under something I learned about Visual C++ programming even though I've been programming it for 15+ years.
OK, so today I'm testing ipPulse 1.70 on different operating systems, Windows 7 (32 & 64), 2008, XP etc. On one completely up to date, fully patched Windows XP system I get the fateful message "cannot find MSVCR90.DLL" blah, blah. I've seen this before. It's the sign of missing side by side DLLs from the SXS directory. But wait! I didn't compile this to use the SXS DLLs - it's all supposed to be static. What's going on?
I started by using the better version of Dependency Walker to check each exe and dll. I find that one dll has the linkage to the SXS directoried (is that a word?) MSVCR90.DLL. So I look at the release flags and for static it is what it should be: /MT. BUGGGER! So next I go to MSDN help pages and carefully review the /MT and /MD flags. I don't see anything obvious, so I remove msvcr90.lib from the linker. Bad idea. Errors galore. I put it back and go back to the docs. I see a reference to libcmt.lib in the same context as /MT. I wonder. I go and remove msvcr90.lib and put libcmt.lib in there instead. The linker loves it. I review the output dll and see the offending SXS linkage is gone. Great! After rebuilding the ipPulse fileset I see that it now runs properly on that other XP system. I never knew that about libcmt.lib and /MT symbiotic relationship. The docs are not clear. So I learned something new today.
I developed ipPulse 1.70 on MS Visual Studio C++ 2008 with static linkage for all files. The DLL in question was pure C. MSVCR90.DLL is the Visual C runtime DLL.
Don't ask me why I didn't use the 2010 compiler.
OK, so today I'm testing ipPulse 1.70 on different operating systems, Windows 7 (32 & 64), 2008, XP etc. On one completely up to date, fully patched Windows XP system I get the fateful message "cannot find MSVCR90.DLL" blah, blah. I've seen this before. It's the sign of missing side by side DLLs from the SXS directory. But wait! I didn't compile this to use the SXS DLLs - it's all supposed to be static. What's going on?
I started by using the better version of Dependency Walker to check each exe and dll. I find that one dll has the linkage to the SXS directoried (is that a word?) MSVCR90.DLL. So I look at the release flags and for static it is what it should be: /MT. BUGGGER! So next I go to MSDN help pages and carefully review the /MT and /MD flags. I don't see anything obvious, so I remove msvcr90.lib from the linker. Bad idea. Errors galore. I put it back and go back to the docs. I see a reference to libcmt.lib in the same context as /MT. I wonder. I go and remove msvcr90.lib and put libcmt.lib in there instead. The linker loves it. I review the output dll and see the offending SXS linkage is gone. Great! After rebuilding the ipPulse fileset I see that it now runs properly on that other XP system. I never knew that about libcmt.lib and /MT symbiotic relationship. The docs are not clear. So I learned something new today.
I developed ipPulse 1.70 on MS Visual Studio C++ 2008 with static linkage for all files. The DLL in question was pure C. MSVCR90.DLL is the Visual C runtime DLL.
Don't ask me why I didn't use the 2010 compiler.
Labels:
DLL hell,
linker,
MFC,
MSVCR90.DLL,
Visual C++ 2008,
Windows XP,
WinSxS
Monday, April 26, 2010
NetScanTools Basic one of 15 recommended tools
NetScanTools Basic was mentioned as number 5 of 15 recommended freeware network tools in the article "Most Wanted Network Tools 100% Freeware". See this blog:
http://www.sialnity.com/2010/04/most-wanted-network-tools-100-freeware/
Have a great week!
Kirk
http://www.sialnity.com/2010/04/most-wanted-network-tools-100-freeware/
Have a great week!
Kirk
Thursday, April 22, 2010
This application has failed to start...
Have you ever seen that message? You know, the one that says "This application has failed to start because the application configuration is incorrect. Reinstalling the application may fix this problem." (that's what it says on Windows XP - Vista and 7 have a more informative message). The message should read: Windows is missing important files that should have been downloaded through automatic updates -- oops!
What this usually means is that the Visual C++ redistributable fileset is wrong, either too old or missing one or more pieces. These are the Side by Side DLLs we are talking about. They reside in the C:\Windows\WinSxS directory and the have rediculously long names. Those names include the version of MFC, runtime, etc of the DLL. This problem happens most often when the compiler has a new revision, like last July 2009's revision of Visual C++ 2005.
Fortunately the fix is pretty simple. You have to find the Visual C++ redistributable installer that is missing and run it. It's installer takes care of the rest and it is a pretty fast fix. But you have to know which one to use. Our software installers look for signs that the SxS DLLs are there, then run the redist installer if they are not found. You may have to contact the software vendor to find out which one to use. Kind of a pain.
I'm posting this because one of our customers had this happen today. Fortunately he emailed and I was able to give him the link to the proper redistributable installer. It fixed his problem.
What this usually means is that the Visual C++ redistributable fileset is wrong, either too old or missing one or more pieces. These are the Side by Side DLLs we are talking about. They reside in the C:\Windows\WinSxS directory and the have rediculously long names. Those names include the version of MFC, runtime, etc of the DLL. This problem happens most often when the compiler has a new revision, like last July 2009's revision of Visual C++ 2005.
Fortunately the fix is pretty simple. You have to find the Visual C++ redistributable installer that is missing and run it. It's installer takes care of the rest and it is a pretty fast fix. But you have to know which one to use. Our software installers look for signs that the SxS DLLs are there, then run the redist installer if they are not found. You may have to contact the software vendor to find out which one to use. Kind of a pain.
I'm posting this because one of our customers had this happen today. Fortunately he emailed and I was able to give him the link to the proper redistributable installer. It fixed his problem.
Labels:
application failed to start,
MFC,
runtime DLLs,
Side by Side DLLs,
SxS
Wednesday, April 21, 2010
Checking Authoritative DNS Serial Numbers
Did you know that Authoritative DNS servers consist of primary and one or more backup or secondary servers? Did you also know that they are supposed to be in sync?
It is important that the servers be in sync. Why? a record in the primary may be very different from the same record in the secondary - especially if it was just changed. A query might get the wrong information (like an IP) if the secondary returns the record instead of the primary. That's why it is important to sync them fairly quickly.
The DNS servers are listed when you do a 'whois' query for a domain. Most domains have only two, a primary and secondary. When changes are made to the primary, then they are migrated to the secondary so that if for some reason the primary does not respond to DNS queries, the secondary may continue to do so.
It is important to know if those primary and secondary servers are in sync. You can look at the SOA serial field to find out. Normally they are identical for all DNS servers. If they are not, then that indicates a problem. You can use NSLOOKUP to retrieve the SOA records from each DNS (primary and secondary). This is a tedious process if there are more than two servers to look at.
We have a tool in NetScanTools Pro that simplifies this process by doing the queries for you very quickly. That way you can see a quick snapshot of the DNS update situation. It is part of the DNS Tools - Advanced and it is called "Auth Serial Check".
Here in this example for our domain showing matching serials. Note that the program looks that them to make sure they are OK:
[Start Query]
Authoritative DNS Serial Check
Starting Timestamp: 04/21/10 17:00:28
Query: netscantools.com
NS: ns2.webnethost.net -- Serial: 2010020400
NS: ns1.webnethost.net -- Serial: 2010020400
Analysis: All serial numbers are identical, no problems detected.
[End Query]
And now here is a query showing microsoft.com's DNS serials. Note that certain DNS servers are out of date with others. "ns1" is the primary and the others are backup.
[Start Query]
Authoritative DNS Serial Check
Starting Timestamp: 04/21/10 16:44:23
Query: microsoft.com
NS: ns3.msft.net -- Serial: 2010042102
NS: ns5.msft.net -- Serial: 2010042101
NS: ns1.msft.net -- Serial: 2010042102
NS: ns4.msft.net -- Serial: 2010042102
NS: ns2.msft.net -- Serial: 2010042101
Analysis: One or more serial numbers are out of sync with the other serial numbers.
[End Query]
I checked again 15 minutes later and found that all DNS serials in the microsoft.com listing were the same. This is probably normal for a domain of this size because it may take awhile to transfer the zone updates from the primary to the secondaries. I checked the SOA record and I could see that the refresh interval is 5 minutes and the retry interval is 10 minutes, so their DNS should not be out of sync for long. It's unusual to see this, so I thought it would make a good example.
A note about the serial field formatting. These both conform to what is now recommended where the serial is human readable. In the case of microsoft.com, you can see that it is April 21 2010, update numbers 1 and 2. In the case of netscantools.com, you can see that the serial has not changed since February 4, 2010. Not all serials conform to this method. Some are just straight incremental numbers.
You can try out the Auth Serial Check tool in the NetScanTools Pro Demo at our website.
It is important that the servers be in sync. Why? a record in the primary may be very different from the same record in the secondary - especially if it was just changed. A query might get the wrong information (like an IP) if the secondary returns the record instead of the primary. That's why it is important to sync them fairly quickly.
The DNS servers are listed when you do a 'whois' query for a domain. Most domains have only two, a primary and secondary. When changes are made to the primary, then they are migrated to the secondary so that if for some reason the primary does not respond to DNS queries, the secondary may continue to do so.
It is important to know if those primary and secondary servers are in sync. You can look at the SOA serial field to find out. Normally they are identical for all DNS servers. If they are not, then that indicates a problem. You can use NSLOOKUP to retrieve the SOA records from each DNS (primary and secondary). This is a tedious process if there are more than two servers to look at.
We have a tool in NetScanTools Pro that simplifies this process by doing the queries for you very quickly. That way you can see a quick snapshot of the DNS update situation. It is part of the DNS Tools - Advanced and it is called "Auth Serial Check".
Here in this example for our domain showing matching serials. Note that the program looks that them to make sure they are OK:
[Start Query]
Authoritative DNS Serial Check
Starting Timestamp: 04/21/10 17:00:28
Query: netscantools.com
NS: ns2.webnethost.net -- Serial: 2010020400
NS: ns1.webnethost.net -- Serial: 2010020400
Analysis: All serial numbers are identical, no problems detected.
[End Query]
And now here is a query showing microsoft.com's DNS serials. Note that certain DNS servers are out of date with others. "ns1" is the primary and the others are backup.
[Start Query]
Authoritative DNS Serial Check
Starting Timestamp: 04/21/10 16:44:23
Query: microsoft.com
NS: ns3.msft.net -- Serial: 2010042102
NS: ns5.msft.net -- Serial: 2010042101
NS: ns1.msft.net -- Serial: 2010042102
NS: ns4.msft.net -- Serial: 2010042102
NS: ns2.msft.net -- Serial: 2010042101
Analysis: One or more serial numbers are out of sync with the other serial numbers.
[End Query]
I checked again 15 minutes later and found that all DNS serials in the microsoft.com listing were the same. This is probably normal for a domain of this size because it may take awhile to transfer the zone updates from the primary to the secondaries. I checked the SOA record and I could see that the refresh interval is 5 minutes and the retry interval is 10 minutes, so their DNS should not be out of sync for long. It's unusual to see this, so I thought it would make a good example.
A note about the serial field formatting. These both conform to what is now recommended where the serial is human readable. In the case of microsoft.com, you can see that it is April 21 2010, update numbers 1 and 2. In the case of netscantools.com, you can see that the serial has not changed since February 4, 2010. Not all serials conform to this method. Some are just straight incremental numbers.
You can try out the Auth Serial Check tool in the NetScanTools Pro Demo at our website.
Labels:
AXFR,
DNS,
DNS Tools,
NetScanTools Pro,
nslookup,
zone serials,
Zone Transfer
Tuesday, April 13, 2010
Malformed UDP Packets
Malformed UDP Packets are easily generated with the new changes to the Packet Generator tool in NetScanTools Pro 10.96.1. Normally a UDP packet consists of an IP header followed by a UDP header followed by data. Usually all the parameters of those two headers are calculated at the time the packet is sent by the sockets layer, but with our Packet Generator tool we can create the packet from beginning to end including all parts of the headers.
This view from Wireshark shows a normal UDP packet:

You can see that the packet is complete and correct with all checksums and field lengths normal. The payload is only 4 bytes - it is the word 'test'.
Now look what happens if we put a value of 2 bytes into the UDP length field - remember that the UDP header itself is 8 bytes. The data payload is still the same 4 bytes. Wireshark's 'Expert Info' analyzer tells us that it is malformed and the length value is the culprit. The checksum is not analyzed and the data is not commented on.

See how Wireshark complains that the length value is less than the data and the UDP header? The message it gives is correct, the UDP length field must have a value of 8 or greater because that is the size of the UDP header itself. Can you send a UDP packet without any data? -sure, but it will also be tagged as malformed by Wireshark (exception error).
Next let's try setting the UDP header length field to something greater than the UDP header length + the data payload length. You can see that it notes that the length value (24) is greater than the payload (8 UDP header + 4 data = 12 bytes) and it does not complete the checksum calculation since all the data is not present.

A few words about what the Packet Generator tool can do. It can generate TCP, UDP, ICMP and CDP packets and send them out at a maximum repetition rate of roughly 10,000 packets per second - it is not a traffic generator capable of saturating your connection. It has a simple scripting language that allows you to send packets and even do some minor looping or use infinite looping. This is useful for connection test purposes. It uses WinPcap to generate packets, so it is pretty much limited to wired connections, not wireless connections. But even within these limits it really can show the response of applications or devices to malformed packets.
If you are interested in trying out the demo, you can do that by following this link. Please keep in mind that the demo will limit you to your local subnet but the full version does not have this limitation.
This view from Wireshark shows a normal UDP packet:

You can see that the packet is complete and correct with all checksums and field lengths normal. The payload is only 4 bytes - it is the word 'test'.
Now look what happens if we put a value of 2 bytes into the UDP length field - remember that the UDP header itself is 8 bytes. The data payload is still the same 4 bytes. Wireshark's 'Expert Info' analyzer tells us that it is malformed and the length value is the culprit. The checksum is not analyzed and the data is not commented on.

See how Wireshark complains that the length value is less than the data and the UDP header? The message it gives is correct, the UDP length field must have a value of 8 or greater because that is the size of the UDP header itself. Can you send a UDP packet without any data? -sure, but it will also be tagged as malformed by Wireshark (exception error).
Next let's try setting the UDP header length field to something greater than the UDP header length + the data payload length. You can see that it notes that the length value (24) is greater than the payload (8 UDP header + 4 data = 12 bytes) and it does not complete the checksum calculation since all the data is not present.

A few words about what the Packet Generator tool can do. It can generate TCP, UDP, ICMP and CDP packets and send them out at a maximum repetition rate of roughly 10,000 packets per second - it is not a traffic generator capable of saturating your connection. It has a simple scripting language that allows you to send packets and even do some minor looping or use infinite looping. This is useful for connection test purposes. It uses WinPcap to generate packets, so it is pretty much limited to wired connections, not wireless connections. But even within these limits it really can show the response of applications or devices to malformed packets.
If you are interested in trying out the demo, you can do that by following this link. Please keep in mind that the demo will limit you to your local subnet but the full version does not have this limitation.
Labels:
malformed packet,
NetScanTools Pro,
packet generator,
UDP,
Wireshark
NetScanTools Pro 10.96.1 Published
Yes, this is a new release: 10.96.1.
It's only been a few days since 10.96 was released, but last week a customer came to us with an important suggestion that we had to implement. The new change is in the UDP section of Packet Generator. At the customer's suggestion we added the ability to override and change the length field in the UDP header. A byproduct of this change is that the text or file data you add to the UDP packet payload is sent in it's entirety (up to the limit of your network MTU) independent of what the IP header length or UDP header length values are. Try this out using Wireshark to look at the UDP packets - Wireshark points out the packet errors you create quite well - lots of red highlighting. There were also other changes to Packet Generator in 10.96 in case you missed them. I'll be writing about this in the blog later today - click on Welcome group, then on the Blog icon.
What does this mean? it means that you now can easily create malformed UDP packets (Laura Chappell loves these).
There is also another change to the automatic checking for a new software version that you can review in the help file under General Information/Revision History.
Because these changes interrupted our normal release sequence we never did release a USB version 10.96 patch. That version was skipped for the USB version so we will be getting the 10.96.1 USB patch out shortly.
To get this new version:
From within NetScanTools Pro, please click on the left panel Welcome or Online group and then click on the Check for New Version icon. Login to obtain the updates. This upgrade is only available to persons with active maintenance plans.
It's only been a few days since 10.96 was released, but last week a customer came to us with an important suggestion that we had to implement. The new change is in the UDP section of Packet Generator. At the customer's suggestion we added the ability to override and change the length field in the UDP header. A byproduct of this change is that the text or file data you add to the UDP packet payload is sent in it's entirety (up to the limit of your network MTU) independent of what the IP header length or UDP header length values are. Try this out using Wireshark to look at the UDP packets - Wireshark points out the packet errors you create quite well - lots of red highlighting. There were also other changes to Packet Generator in 10.96 in case you missed them. I'll be writing about this in the blog later today - click on Welcome group, then on the Blog icon.
What does this mean? it means that you now can easily create malformed UDP packets (Laura Chappell loves these).
There is also another change to the automatic checking for a new software version that you can review in the help file under General Information/Revision History.
Because these changes interrupted our normal release sequence we never did release a USB version 10.96 patch. That version was skipped for the USB version so we will be getting the 10.96.1 USB patch out shortly.
To get this new version:
From within NetScanTools Pro, please click on the left panel Welcome or Online group and then click on the Check for New Version icon. Login to obtain the updates. This upgrade is only available to persons with active maintenance plans.
Thursday, April 8, 2010
NetScanTools Pro 10.96 Published
On April 6, 2010, we put the finishing touches on NetScanTools Pro 10.96. This is a minor release that does add one new feature plus several improvements to existing tools.
That new feature is the ability to save optional MD5 hash signature (checksum) files when you save text results, databases or packet capture files to disk. The MD5 file is a text file with the MD5 signature in it. This feature is particularly useful to those in law enforcement.
Improvements are in several areas, particularly Packet Generation and Capture. In the Packet Generator we have improved the scripting so that you can now do simple looping X number of times or you can do an infinite loop making it easy to send repeating sets of packets to a target. Packet Generator also now tells you if WinPcap fails to send a packet. By altering the display update of the floating packet send info window, we have been able to drastically speed up the sending of packets in continuous packet send mode.
In Packet Viewer (to be renamed Packet Capture in version 11), there were considerable improvements made to the parsing of IGMP packets and also the program now recognizes HP Switch LLC packets and Spanning Tree Protocol packets.
There are other minor things like NetBIOS Basic now reporting Windows 7 machines instead of "Windows 6.1". Clear buttons were added to the Whois and Real Time Blacklist (RBL) check tools next to the DNS IP address entry boxes.
One more interesting issue came from a tech support call I had a couple months ago. The user told me that he had a multihomed (more than one active network interface) machine and he was trying to either capture or send packets - I can't exactly remember. Anyway, it appears that the first option in the dropdown WinPcap Interface selection box was "169.254.7.179" - he said that he got an error message when trying to use that interface. After some discussion, we found there was a second IP in the dropdown box - he selected that one and everything worked.
As you may know, the 169.254.x.x IPs are what Windows assigns when it fails to get a new IP from DHCP - this is Automatic Private IP Addressing. So what was added to NetScanTools Pro was this: as the program starts, we go through the list of available interfaces. If a 169.254.x.x interface is found, the user is asked if they want to include it in the list of available WinPcap capable interfaces. Rather than just excluding those from the list, we ask you because someone may actually have set up a network with IPs in that range.
To get this new release you must have an active maintenance plan. If you do, then click on Help/Check for New Version. Login using the credentials shown in the program and download the installer. You will need your CDKEY/Serial Number to install, it is found on Help/About NetScanTools Pro. Please install over the top of your old installation and registering again should not be required.
That new feature is the ability to save optional MD5 hash signature (checksum) files when you save text results, databases or packet capture files to disk. The MD5 file is a text file with the MD5 signature in it. This feature is particularly useful to those in law enforcement.
Improvements are in several areas, particularly Packet Generation and Capture. In the Packet Generator we have improved the scripting so that you can now do simple looping X number of times or you can do an infinite loop making it easy to send repeating sets of packets to a target. Packet Generator also now tells you if WinPcap fails to send a packet. By altering the display update of the floating packet send info window, we have been able to drastically speed up the sending of packets in continuous packet send mode.
In Packet Viewer (to be renamed Packet Capture in version 11), there were considerable improvements made to the parsing of IGMP packets and also the program now recognizes HP Switch LLC packets and Spanning Tree Protocol packets.
There are other minor things like NetBIOS Basic now reporting Windows 7 machines instead of "Windows 6.1". Clear buttons were added to the Whois and Real Time Blacklist (RBL) check tools next to the DNS IP address entry boxes.
One more interesting issue came from a tech support call I had a couple months ago. The user told me that he had a multihomed (more than one active network interface) machine and he was trying to either capture or send packets - I can't exactly remember. Anyway, it appears that the first option in the dropdown WinPcap Interface selection box was "169.254.7.179" - he said that he got an error message when trying to use that interface. After some discussion, we found there was a second IP in the dropdown box - he selected that one and everything worked.
As you may know, the 169.254.x.x IPs are what Windows assigns when it fails to get a new IP from DHCP - this is Automatic Private IP Addressing. So what was added to NetScanTools Pro was this: as the program starts, we go through the list of available interfaces. If a 169.254.x.x interface is found, the user is asked if they want to include it in the list of available WinPcap capable interfaces. Rather than just excluding those from the list, we ask you because someone may actually have set up a network with IPs in that range.
To get this new release you must have an active maintenance plan. If you do, then click on Help/Check for New Version. Login using the credentials shown in the program and download the installer. You will need your CDKEY/Serial Number to install, it is found on Help/About NetScanTools Pro. Please install over the top of your old installation and registering again should not be required.
Thursday, March 18, 2010
Laura Chappell's new Wireshark Network Analysis Book

Laura has done it again. She's written a huge book about Wireshark. When I develop NetScanTools Pro, I use Wireshark to be sure the packets I'm sending and receiving are correct. And NetScanTools Pro saves packet captures in a format that can be opened by Wireshark. I have only read the snippets of the book on the wiresharkbook website, but I can see that the quality is superb and it will be in depth!
You can pre-order the Wireshark Network Analysis book (www.wiresharkbook.com) at a 35% discount using this code:
998NST35 (this is not case sensitive)
Valid until March 29, 2010
Estimated ship date: March 29, 2010
Wireshark Network Analysis: The Official Wireshark Certified Network Analyst Study Guide
Paperback: 800 pages
Publisher: Protocol Analysis Institute
Website: www.wiresharkbook.com
Language: English
ISBN10: 1-893939-99-8
ISBN13: 978-1-893939-99-8
Dimensions: 7.44 x 9.69 inches
Weight: 3.5 pounds
Contact: info@chappellU.com or +1 408-378-7841
Exam Version: Version 1 (WCNA-100 Exam) (Q2 2010 Release)
Exam Link: www.wiresharkU.com/certification.html
Tuesday, March 16, 2010
NetScanTools LE 1.20 Released 3-15-2010
Release 1.20 adds essential hash signature functionality to a program designed for use by Law Enforcement. It now creates a companion MD5 hash signature file for exported text files and for exported packet capture ".cap" files. Hash signatures are now included in the database tables to help assure that the table data has not be changed. The purpose of these signatures is to help assure that data you save has not been altered later. You can use any MD5 hash signature utility to verify the original file signature against the saved hash signature file.
There are also some minor fixes in this release. Email Validate now correctly shows the full details of the validation process. DNS Tools now makes better use of the progress bar. We added Select All and Clear All buttons to the Automated Test selection list.
As usual, all the database files were updated and the SQLite DLL was updated to the latest version.
NetScanTools LE is available at http://www.netscantools.com/nst_le_main.html
There are also some minor fixes in this release. Email Validate now correctly shows the full details of the validation process. DNS Tools now makes better use of the progress bar. We added Select All and Clear All buttons to the Automated Test selection list.
As usual, all the database files were updated and the SQLite DLL was updated to the latest version.
NetScanTools LE is available at http://www.netscantools.com/nst_le_main.html
Labels:
hash,
MD5,
NetScanTools LE,
new release,
signature
Friday, February 5, 2010
Multi-Domain Whois - what is it?

We introduced a new tool in NetScanTools Pro 10.95 called Multi-Domain Whois. It's actually something that we first put in NetScanTools LE 1.00 last month.
First, a little background: one of our longtime law enforcement customers asked for a tool that could take a base domain name like 'netscantools' and do a whois query on netscantools.com, netscantools.net, netscantools.co.uk, etc. He knew that there were online tools for finding out if the domains were registered or not, but he wanted to know the details of each registration without having to manually do a whois query on each one.
Enter Multi-Domain Whois Query. As you can see in the image above you enter the base domain name like 'netscantools' or 'netscantools-le', then you select the extensions you want to query and press Do Multi-Domain Whois. In both NetScanTools Pro and NetScanTools LE it then queries each of those you selected by appending the domain name and querying the right whois server. The results are shown in the display in NetScanTools Pro and saved in the current Case Database in NetScanTools LE. In NetScanTools Pro 10.95, you can review the results by by scrolling the results window on the whois tool page (a query separator is added for clarity). In NetScanTools LE, you click on reports and select the reports you are interested in.

To summarize, Multi-Domain Whois gives you the ability to do a bulk whois query on a number of different common domain extensions using a single input base domain name.
As with all bulk whois queries, be careful how much you use this because whois servers often have query number limits on them. Some are as low as 10 queries per 24 hours - be careful.
Wednesday, February 3, 2010
New DNS Speed Test Tool in NetScanTools Pro 10.95
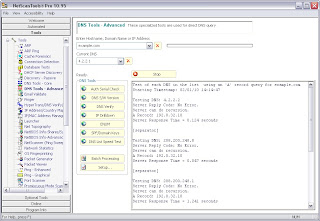
Our good friend Phil at Ford asked us if we could provide a tool that accepted a list of DNS IPs, then test each DNS to find out how fast it could resolve a hostname or an IP address. We did it.
You can find the DNS List Speed Test tool on the DNS Tools - Advanced toolset page. Using it is pretty simple, first create a list of DNS IPv4 Addresses (hostnames can also be used but are discouraged) and save it to a text file. The list should be one IP address per line. Notepad works well for this. Then put in a hostname or an IP in the entry area, and press the DNS List Speed Test button. A File Open navigation window will open, locate and open the text file you just created. The tool will take it from there.
The output area tells you the IP of each DNS being tested, the DNS server reply code, whether or not the DNS can do recursion, and the A or PTR record that matched the input (if available). Sometimes you will see other DNS records like NS decoded if the DNS sent them to you. It also tells you the Server Response Time which is really what you are after. You can see just how fast each DNS server is with this tool.
DNS response time (latency) is most interesting part of the results and the purpose of the tool.. The DNS response time is calculated from the moment we send the packet to the moment a response is received. DNS managers like Phil who manage hundreds of DNS's can see which DNS's are having troubles by quickly looking at the response content and the DNS response time.
You can see the results in the image above.
Labels:
DNS response time,
DNS Speed Test,
DNS Tools,
latency
NetScanTools Pro 10.95 USB Version Patch Ready
The USB version patch is ready. It will upgrade your NetScanTools Pro USB to 10.95. To obtain the patch, login through Help/Check for New Version. You need an active maintenance plan to have access to the upgrade.
NetScanTools Pro 10.95 Published
NetScanTools Pro 10.95 was released late in the day on Monday February 1, 2010. We've added some new tools and made numerous changes to existing tools.
New Tools
-DNS Tools - Advanced: DNS List Speed Test - this tool accepts a list of DNS IPs (hostnames are allowed, but not recommended), then it sends an identical forward or reverse resolve query to each DNS and shows the response time. It also shows the data that each DNS sends back.
-Whois: Multi-Domain Whois - this tool accepts as input a base domain name, like 'netscantools', then it appends a top level domain or secondary level domain extension like '.ca' or '.co.uk' and queries the appropriate whois server. users can select from a large number of extensions to add. The whois queries are done as a group or batch much like the current batch whois tool.
-Whois: Autonomous System Numbers are now accepted as input. Format is AS##### where # are numbers.
If you have an active maintenance plan, click on Help/Check for New Version to download this new version. If you are interested in renewing your maintenance plan or buy the software, please see our website.
New Tools
-DNS Tools - Advanced: DNS List Speed Test - this tool accepts a list of DNS IPs (hostnames are allowed, but not recommended), then it sends an identical forward or reverse resolve query to each DNS and shows the response time. It also shows the data that each DNS sends back.
-Whois: Multi-Domain Whois - this tool accepts as input a base domain name, like 'netscantools', then it appends a top level domain or secondary level domain extension like '.ca' or '.co.uk' and queries the appropriate whois server. users can select from a large number of extensions to add. The whois queries are done as a group or batch much like the current batch whois tool.
-Whois: Autonomous System Numbers are now accepted as input. Format is AS##### where # are numbers.
If you have an active maintenance plan, click on Help/Check for New Version to download this new version. If you are interested in renewing your maintenance plan or buy the software, please see our website.
Labels:
DNS Tools,
NetScanTools Pro,
new release,
whois
Is the economy getting better? part 2
uh...maybe not.
We sent out an announcement yesterday about the release of NetScanTools Pro 10.95 and got back 13 bounced emails. I resent the announcement from an different domain just to be sure it was a real bounce and sure enough, 13 people are no longer employed since the last announcement at the beginning of November 2009.
We sent out an announcement yesterday about the release of NetScanTools Pro 10.95 and got back 13 bounced emails. I resent the announcement from an different domain just to be sure it was a real bounce and sure enough, 13 people are no longer employed since the last announcement at the beginning of November 2009.
Sunday, January 31, 2010
Is the economy getting better?
Maybe. We send out a newsletter once a month and for the end of 2008 and all of 2009, we've had between 10-20 or more email bounce backs each month. While some of those could be bounced back for other reasons, our assumption is that the person is no longer at their job. Keep in mind that most of the email addresses in our list are business addresses and not personal home email addresses.
So a few days ago I sent out the January 2010 newsletter and I only had 3 'user unknown' email bounces. December 2009 was under 10, but only a little. A definite improvement.
Here is the January 2010 newsletter if you are interested:
http://www.netscantools.com/pressandnewsletters/NST_Pro_January_2010_News.pdf
I guess I could call this the "Email Bounce Economic Index".
So a few days ago I sent out the January 2010 newsletter and I only had 3 'user unknown' email bounces. December 2009 was under 10, but only a little. A definite improvement.
Here is the January 2010 newsletter if you are interested:
http://www.netscantools.com/pressandnewsletters/NST_Pro_January_2010_News.pdf
I guess I could call this the "Email Bounce Economic Index".
Saturday, January 16, 2010
NetScanTools (tm) Basic Edition 2.0 Released Jan 14, 2010

This update to the Freeware Basic Edition changes the layout of the left control panel to make it less confusing. I also added the registered trademark notice for NetScanTools. The SQLite DLL to the latest version as was the whois database it works with. The biggest change was a switch to Inno Setup away from the old Wise installer. This reduced the size of the final installation .exe nearly 1 MB and it gives full compatibility with Windows 7. Speaking of Windows 7, NetScanTools Basic is fully Windows 7 compatible.
You can get NetScanTools Basic 2.0 here.
Labels:
DNS,
NetScanTools Basic,
Ping,
Ping Scan,
SQLite,
traceroute,
whois
Friday, January 15, 2010
NetScanTools LE 1.10 Released 1-12-2010

We released NetScanTools Law Enforcement (LE) v1.00 on Jan 1 and we quickly heard from our friends at a government training center that they would really like to have a basic packet capture tool in it.
We had planned on putting in Packet Capture for the purpose of showing that the evidence in the reports could be substantiated and validated if required. The Packet Capture tool is currently independently run from the main program, so in order to validate your work, you would need to start it before you work on a task. That way you would collect the same packet information and save it. The Packet Capture trace file MUST be saved separately when you are done with your tasks, this is not automatic at the moment.
Packet Capture files are 100% Wireshark compatible, so if you need to show a chain of communication in the process of retrieving information from external network sources, you can do so using that free packet analysis tool. Our Packet Capture tool has a basic packet viewer so you can see the contents of the packets and search for something within a packet.
At some point the Packet Capture tool will be better integrated. Maybe in the next version.
You can read about NetScanTools LE and download a 30 day trial here:
http://www.netscantools-le.com/
NetScanTools LE v1.10 was released on Jan 14, 2010.
Monday, January 11, 2010
SNMP Scanning
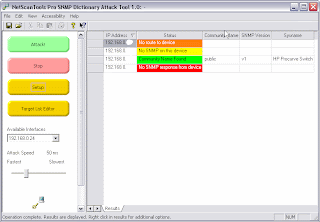
What do we mean by SNMP Scanning? For the purposes of this article, it means scanning a range of IP addresses to see what devices are running SNMP servers. Some people call this SNMP Community Name guessing or bruteforcing.
What is SNMP and what is it used for? SNMP stands for Simple Network Management Protocol. It's used by network devices like routers and switches to report information about the device. Even a Windows computer can be made to divulge information using SNMP! (Windows does not install it by default). This information can be device information like temperature, packet counts or packet statistics or even IP addresses of devices connected to the device. The info is arranged in a heirarchical order somewhat like directories on a hard drive.
SNMP comes in 3 flavors or versions: 1, 2c and 3. Most devices support 1 and 2c, while newer devices will support v3 and usually have backwards compatibility with versions 1 and 2c. Versions 1 and 2c are very similar and report data to a client if the client includes a simple plain text password-like phrase called a 'community name'. We're going to limit our discussion to v1 and v2c.
SNMP usually runs on UDP port 161. Some people like to put it on an alternate UDP port to avoid what we are going to do in this article. Since it's a UDP based protocol, there is no full connection, so when we talk to an SNMP server it won't respond to us unless the question we are asking is correct. There are two essential parts of the question: the MIB item we are asking for and the community name (password) to get it. Both have to be correct to get a good response.
Back to the point of this article. How do you find the devices in your network running SNMP? One way is to do a Port Scan of every device in the IP range on port 161. This might work, but since SNMP is UDP you are depending on the targets returning an ICMP Port Unreachable message to you if the device is NOT running SNMP. This is a lot to ask, especially if the devices have a firewall or are set to not reply with ICMP. You run the risk of lots of false positives with port scanning.
Another way is to use a specialized tool called SNMP Dictionary Attack which is part of NetScanTools Pro. This tool can make an SNMP query to each IP address and it can send known or common community names to the devices. If you are a network administrator, you already know what the community names of your devices are, so here's a shortcut that you may want to try (if not, then skip this). Locate dctnry.txt in your NetScanTools Pro installation directory and open it with notepad. Enter your common community names at the beginning of the list, one per line and save it (we are going to improve this soon).
Using NetScanTools Pro to scan for SNMP servers on devices. Start NetScanTools Pro and locate the SNMP tools under the Tools left panel group. Select Dictionary Attack under the dropdown list labeled Select SNMP Action. Press Perform Action (no other settings are necessary). This opens the tool.
Now press the Target List Editor button on the left panel to open the editor. You can do one of several things here. You can enter IP addresses one at a time or you can define a range of IPs or you can import a list of IPs. The bigger the list, the longer the scan takes - recommend 256 or less IPs. Once you have created your list press OK and then press Setup. In Setup you can define the SNMP version(s) you want to use. If you choose both v1/v2c, it takes twice as long to scan. You can also adjust the time to wait for an SNMP response. Once you are satisfied with the values, press OK and now we are ready. Put the 'Attack Speed' in the middle range and press the 'Attack' button.
The scan proceeds with the results being presented in the grid as they are found. If the device responds to the SNMP queries, you will see 'Community Name Found' along with the community name, version and system name. If not, you will see 'No SNMP on this device' if an ICMP message came back. You may also see a definitive 'No route to device' if you are on the same subnet as the device. If you edited the dictionary list first, this process will go pretty quickly if you are on the same subnet, but it may take awhile if you are scanning devices outside your subnet.
You can watch the scan status on the lower bar. This tool will work best on the same subnet as the devices, but it is not limited to that subnet (the demo version is limited to the local subnet). While you watch it scan, if the device status is blank, it will continue to try community names until it exhausts the list or the device responds.
When you are done or when you feel the scan has gone on long enough, you can review the results. You should be able to see which devices are running SNMP and their community names.
This is a brute force password guessing tool that will show SNMP responses if the device is running SNMP and you have the correct community name. It scans a list of IP addresses and tests them with multiple SNMP queries in an attempt to get a response. It can take awhile and the community name may not be in the dictionary, so you may not be able to find the community name. We have created a fairly comprehensive list and it does cover many common passwords like the default 'public' and 'private'. Try out the tool in our demo or if you have the full version, give it a try. The demo is here: http://www.netscantools.com/nstprodemorequest.html
As with all scanning tools, we must warn you that your actions may be construed as hostile and may violate local laws. So you need to limit your scans to your own systems or have the permission of the IP address range owner before scanning. There will be lots of traffic directed toward the SNMP port, so intrusion detection systems (IDS) will see it. This is not a stealthy scan operation.
Labels:
brute force,
dictionary attack,
DNS Tools,
MIBs,
NetScanTools Pro,
scanning,
SNMP
Friday, January 1, 2010
NetScanTools LE Released!
January 1, 2010
Northwest Performance Software, Inc. announces the release of NetScanTools LE 1.00. LE = Law Enforcement.
NetScanTools LE is an Internet Information Collection tool that gives you reports about an IP Address, Hostname, Domain Name, Email Address or URL (web address). This is NetScanTools designed especially for Law Enforcement. We asked our Law Enforcement NetScanTools Pro users what tools they really needed. We took their favorite tools, streamlined them into a new interface and made the program 'case' oriented. And 'case' oriented means that all your queries are documented, time stamped and saved automatically. Reports are direct and to the point. There are no distractions in the reports - you get the results you need, not fancy logos.
For more information and to request a 30 day trial, please visit: http://www.netscantools-le.com/
Kirk Thomas
Northwest Performance Software, Inc. announces the release of NetScanTools LE 1.00. LE = Law Enforcement.
NetScanTools LE is an Internet Information Collection tool that gives you reports about an IP Address, Hostname, Domain Name, Email Address or URL (web address). This is NetScanTools designed especially for Law Enforcement. We asked our Law Enforcement NetScanTools Pro users what tools they really needed. We took their favorite tools, streamlined them into a new interface and made the program 'case' oriented. And 'case' oriented means that all your queries are documented, time stamped and saved automatically. Reports are direct and to the point. There are no distractions in the reports - you get the results you need, not fancy logos.
For more information and to request a 30 day trial, please visit: http://www.netscantools-le.com/
Kirk Thomas
Happy New Year!
Wishing you a good and prosperous 2010!
Subscribe to:
Comments (Atom)
